Designing a Secure Multi-VPC Architecture with AWS Transit Gateway and IGW
Preface
In an AWS cloud Proof of Concept (PoC), Transit Gateway (TGW) and Internet Gateway (IGW) are key to secure, scalable and efficient communication between different VPCs and external networks. Transit Gateway (TGW) is a central routing hub where multiple VPCs can communicate without the complexity of multiple VPC peering connections. It simplifies network management, scales and enforces security policies through route tables to control traffic between connected VPCs. Internet Gateway (IGW) is required for outbound and inbound internet access for resources in public subnets. It allows public facing workloads like web servers and APIs to talk to external services while keeping private subnets secure through NAT Gateways. Together TGW and IGW provide a structured and controlled networking environment, so critical workloads are secure, isolated when needed and connected efficiently in a multi-VPC architecture.
POC
The proposed Proof of Concept (PoC) focuses on establishing secure and controlled communication between multiple VPCs using AWS Transit Gateway (TGW) and Internet Gateway (IGW) in the US-EAST-1 region. The architecture consists of three VPCs: GTPL_NOC (10.1.1.0/24), GTPL_SOC (10.1.2.0/24), and GTPL_ADM (10.1.3.0/24), with TGW (
GTPL_TGW_US-EAST-1) acting as the central routing hub. GTPL_NOC and GTPL_ADM are connected via TGW, enabling seamless communication, while GTPL_SOC remains isolated with no TGW attachment to enforce strict security policies. An Internet Gateway (GTPL_IGW_US-EAST-1) is attached to GTPL_NOC to facilitate external connectivity, allowing public-facing resources in the GTPL_NOC Public Subnet (10.1.1.0/28) to access the internet. Private subnets in GTPL_ADM (10.1.3.0/28) can leverage a NAT Gateway in GTPL_NOC for outbound internet access without exposing internal resources. By implementing TGW route tables and security policies, the setup ensures efficient inter-VPC communication while maintaining strict isolation for GTPL_SOC. This PoC serves as a scalable network foundation, enabling controlled access to internet services while securing sensitive workloads in a multi-VPC environment.Implementation steps of POC
Step-1: Create VPC for GTPL_NOC
Step-3: Create VPC for GTPL_ADMIN
Step-4: Create transit Gateway of GTPL_TGW
Step-6: Create Public subnet for GTPL_SOC
Step-7: Create Private subnet for GTPL_ADMIN
Step-8 Attach GTPL_NOC_VPC with TGW
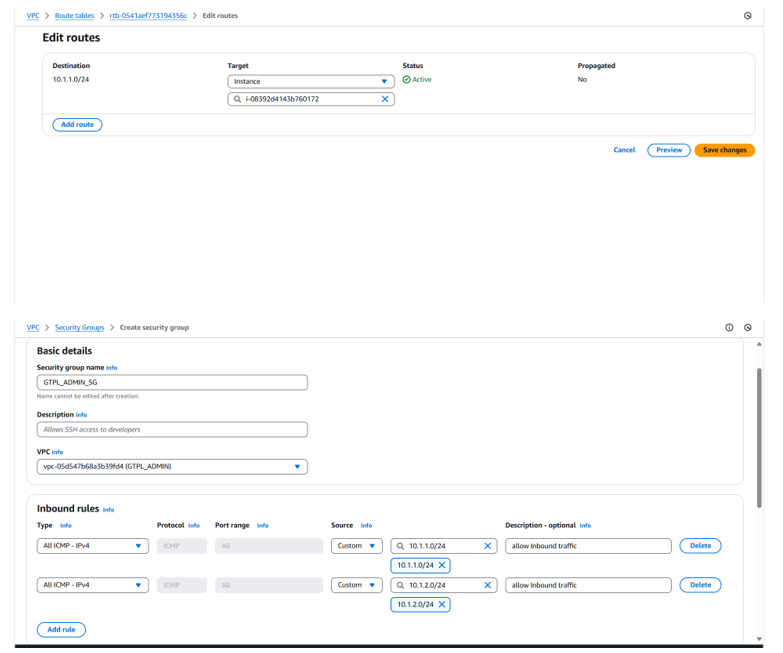
STEP-10 create security group with inbound and outbound traffic rule of GTPL_NOC
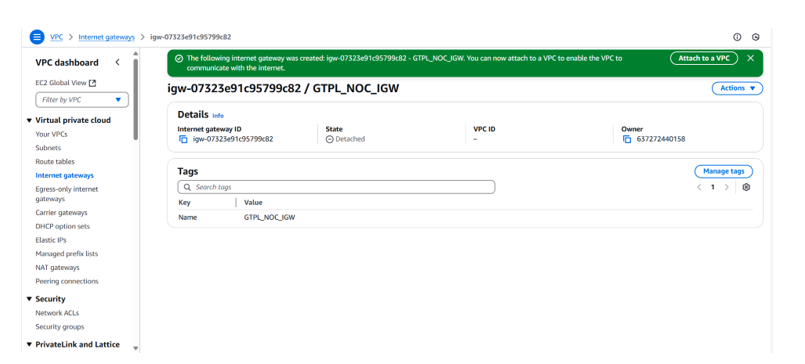
STEP-13 Create GTPL_NOC_IGW for outbound traffic towards internet
STEP-14 Select GTPL_NOC VPC and attached with GTPL_NOC_IGW
wrap-up:
✅
❌
❌
GTPL_NOC → IGW for Internet Access❌
GTPL_SOC → No IGW, Fully Isolated❌
GTPL_ADM → No IGW, Use NAT if needed1. Previous all steps need to be followed from Admin department towards NOC department except IGW.
2. Here, SOC department remains isolated.
3. As per requirement wise need to apply Inbound and outbound traffic policy then create security group appropriately.
4. As per Policy and POC wise VPC need to attach with security group.
6. with the help of ICMP reachability we can cross-verify architecture wise POC.



















Comments
Post a Comment